
Biometric devices are used to distinguish individuals by the different features in their body, which includes face, fingerprints, hand- geometry, voice recognition and eye (iris or retinal) scans. Every individual consists of unique characteristics, which ensures in providing security because it cannot be copied or shared by another person. Fingerprint scanning is an accurate and common biometric that is used by millions of people worldwide. Large corporations, police, prisons and airports are using this device to identify an individual from another.
Fingerprints are considered unique because no two fingers can have the same characteristics. There are five patterns to distinguish an individual’s fingerprint such as left loop, rig
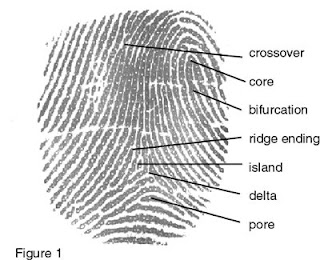 ht loop, whorl, arch and tented arch. In order to determine the exclusiveness of a fingerprint the following are considered minutiae points along with the patterns of ridges and furrows. All fingerprints consist of 60% of loops, 30% of whorls and 10% of arches. Figure 1, shows the many types of characteristics a fingerprint is made up of which makes this device reliable and dependable because not one individual can have the same patterns of another.
ht loop, whorl, arch and tented arch. In order to determine the exclusiveness of a fingerprint the following are considered minutiae points along with the patterns of ridges and furrows. All fingerprints consist of 60% of loops, 30% of whorls and 10% of arches. Figure 1, shows the many types of characteristics a fingerprint is made up of which makes this device reliable and dependable because not one individual can have the same patterns of another.Fingerprint systems can be used as an identification mode, where an individual is identified from the entire population. Once the fingerprint is scanned, it is primarily searched in the database for a match based on their individual characteristic. This is known as one- to- many matching. It can also be used as a verification mode where a person authenticates their identity from their prior enrolled pattern, which is also known as one- to- one matching. The scanner can authenticate the user with a simple finger touch. Primarily, the device scans and captures the unique pattern of ridges and valleys that consist in the individual’s fingerprint. The scanning device then processes, stores and compares the collected data with the stored data. Finally, when the fingerprint match has been confirmed, access is granted.
The figure below demonstrates the three simple steps of how scanners record identities.

References
-http://www.questbiometrics.com/biometric-definition.html
-http://www.biometricnewsportal.com/biometrics_benefits.asp
-http://www.trimso.com/finger_bio.html
-http://www.globalsecurity.org/security/systems/biometrics.htm
-http://news.bbc.co.uk/1/hi/technology/6170070.stm-http://bizsecurity.about.com/od/windowsdesktopsecurity/a/fingerscanner.htm
-http://uk.gizmodo.com/2006-3-30-fingerprint.jpg
http://www.itgi.org/Template.cfm?Section=Home&CONTENTID=34319&TEMPLATE=/ContentManagement/ContentDisplay.cfm

No comments:
Post a Comment